39 aws security best practices
12 Important AWS Security Best Practices for 2022 An AWS security best practice is giving individual identities, whether they are people or pieces of compute, the exact amount of privileges they need to get their job done and removes the privileges when no longer needed. Discover and Inventory All Identities You can only protect or manage accounts, identities, roles, and assets that you can see. Establishing your best practice AWS environment AWS recommends that you start with security and infrastructure in mind. Most businesses have centralized teams that serve the entire organization for those needs. As such, we recommend creating a set of foundational OUs for these specific functions: Infrastructure: Used for shared infrastructure services such as networking and IT services.
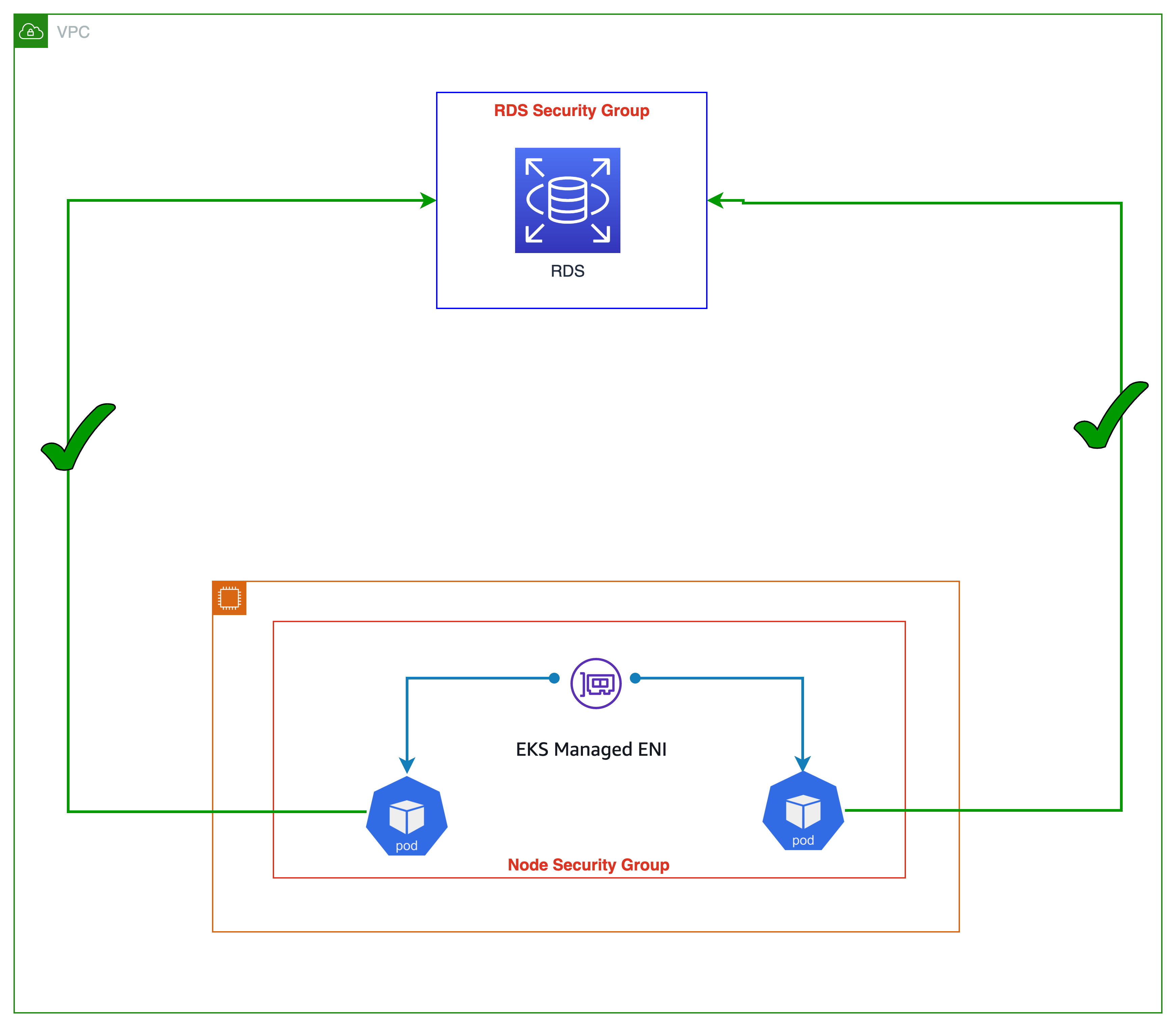
AWS Security Group Best Practices | Cy5 AWS Security Group Best Practices Restrict Default Security Groups. Each VPC in a region comes with a default security group. One can identify it by looking at the security group name field as default in the list of available security groups. This default SG has following characteristics: Allows all Outbound/Egress traffic.

Aws security best practices
Best practices for securing sensitive data in AWS data stores AWS Identity and Access Management (IAM): Define, enforce, and audit user permissions across AWS services, actions, and resources. Detective control: Improve your security posture, reduce the risk profile of your environment, and gain the visibility you need to spot issues before they impact your business. 🔥 Security Best Practices for AWS Users - azumo.com It is essential that AWS users understand the importance of security in the cloud environment and take the necessary steps to protect their data and resources. This article will provide an overview of security best practices for AWS users, covering topics such as access control, logging and monitoring, encryption, and data protection measures. 10 AWS Security Audit Best Practices - CLIMB In this article, we'll discuss 10 AWS security audit best practices that you should consider when conducting an audit. We'll cover topics such as identity and access management, logging and monitoring, and encryption. By following these best practices, you can ensure that your cloud environment is secure and compliant. 1.
Aws security best practices. 13 AWS Security Best Practices - Check Point Software Perform Threat Hunting in AWS: A fully reactive cybersecurity policy, based on identifying and responding to in-progress attacks, places the organization at risk. By the time an attack has been identified, the attacker likely already has access to the organization's cloud-based infrastructure and is stealing data or causing other harm. Top 10 AWS Security Best Practices - easydeploy.io An AWS security best practices checklist includes the focus on shared responsibility, thereby communicating the customer's share of responsibilities. Amazon takes care of security for managed services while customers have to look after the security of unmanaged AWS services. 2. Multi-factor Authentication. 10 AWS DevOps Security Best Practices - CLIMB To ensure that your AWS environment is secure, you should regularly review and remove any unused credentials. This includes user accounts, access keys, and other authentication methods. You should also make sure to rotate credentials on a regular basis, so that if an account is compromised, the damage is limited. AWS Foundational Security Best Practices controls The AWS Foundational Security Best Practices standard contains the following controls. For each control, the information includes the following information. The category that the control applies to. For descriptions of the categories, see Control categories. The severity The applicable resource that the control evaluates.
AWS Cloud Security Best Practices | CrowdStrike Guilherme (Gui) Alvarenga, is a Sr. Product Marketing Manager for the Cloud Security portfolio at CrowdStrike. He has over 15 years experience driving Cloud, SaaS, Network and ML solutions for companies such as Check Point, NEC and Cisco Systems. He graduated in Advertising and Marketing at the Universidade Paulista in Brazil, and pursued his ... PDF AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 1 Introduction Information security is of paramount importance to Amazon Web Services (AWS) customers. Security is a core functional requirement that protects mission- critical information from accidental or deliberate theft, leakage, integrity compromise, and deletion. AWS Security Group: Best Practices & Instructions - CoreStack Best Practice. Using the AWS default security group for active resources. New instances can adopt the group by default - potential unintentional security compromise. Create new security groups and restrict traffic appropriately. Allow all inbound access (using 0.0.0.0/0) to some or all ports. AWS Security Best Practices | Classroom Training | AWS Students should have familiarity with AWS services and a strong background in information security concepts, techniques, and paradigms in the areas of networking, operating systems, data encryption, and operational controls. We recommend that attendees of this course have completed: AWS Security Fundamentals AWS Security Essentials Find a class
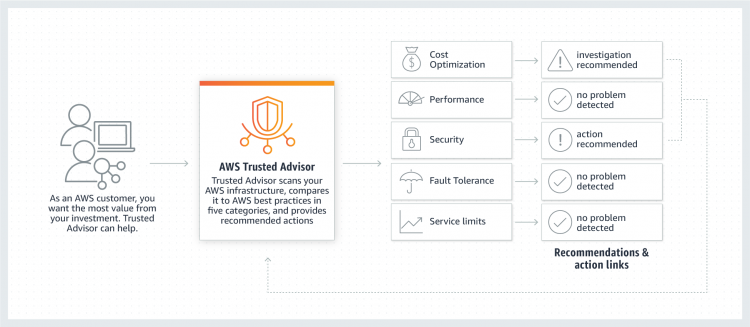
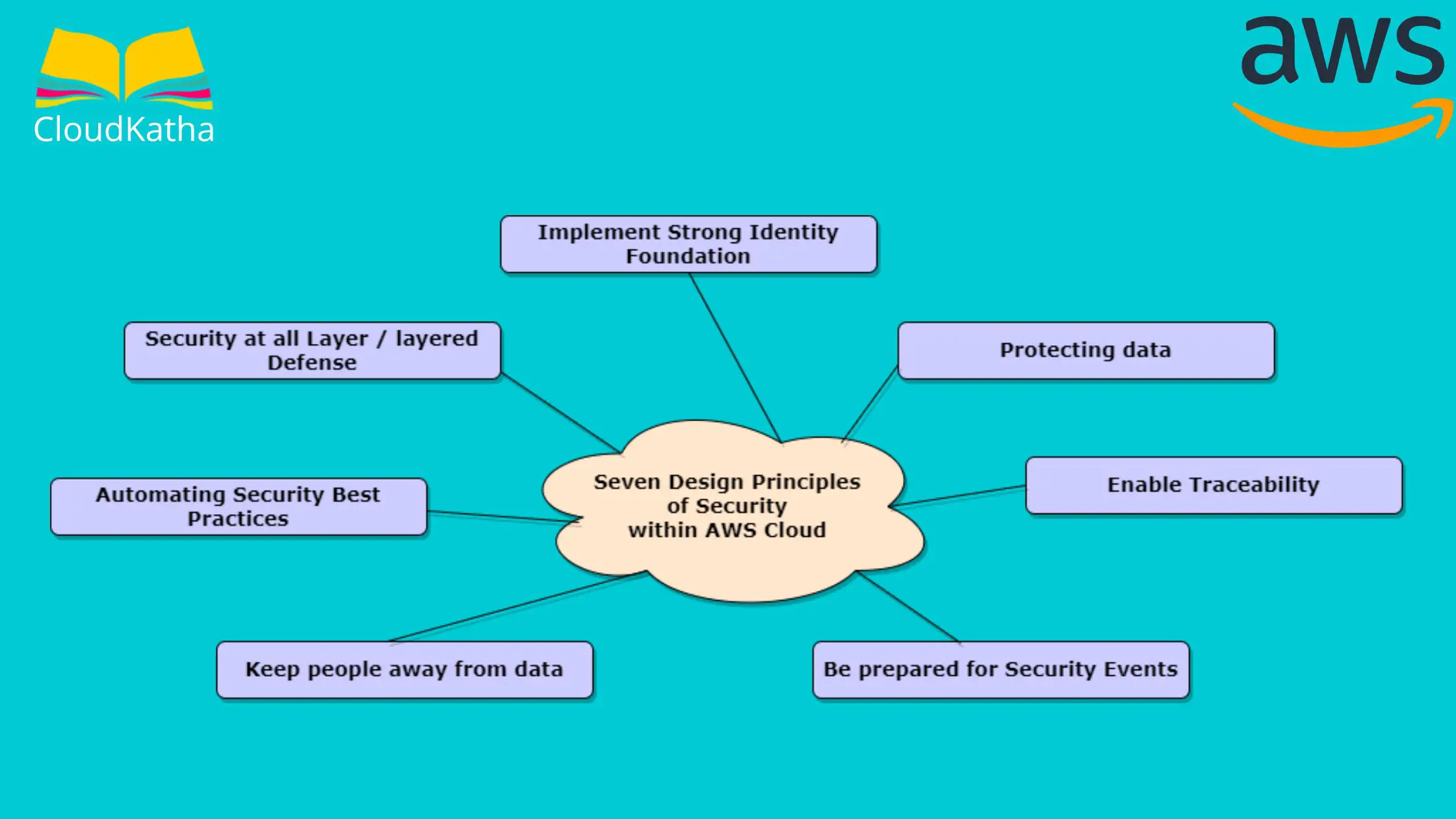
AWS Foundational Security Best Practices standard The AWS Foundational Security Best Practices standard is a set of controls that detect when your deployed accounts and resources deviate from security best practices. The standard allows you to continuously evaluate all of your AWS accounts and workloads to quickly identify areas of deviation from best practices. AWS Security Best Practices AWS Security Best Practices Report this post ... This framework is designed to help compare your infrastructure against industry best practices and identify any weaknesses or areas for improvement. 10 AWS Security Architecture Best Practices - CLIMB Review the rules in your security groups regularly, and ensure that you apply the principle of least privilege - only open up permissions that you require Security groups are the first line of defense for your AWS environment, and they control inbound and outbound traffic to and from your resources. What is AWS Security? Risks, Best Practices, and More - Digital Guardian Best Practices for AWS Security In August 2016, Amazon released a 74-page document detailing the best practices for AWS users. Some of the biggest takeaways are: Think of security at every layer. Instead of using just one firewall to secure all of your virtual networks, be sure to use virtual firewalls on every network that you create.
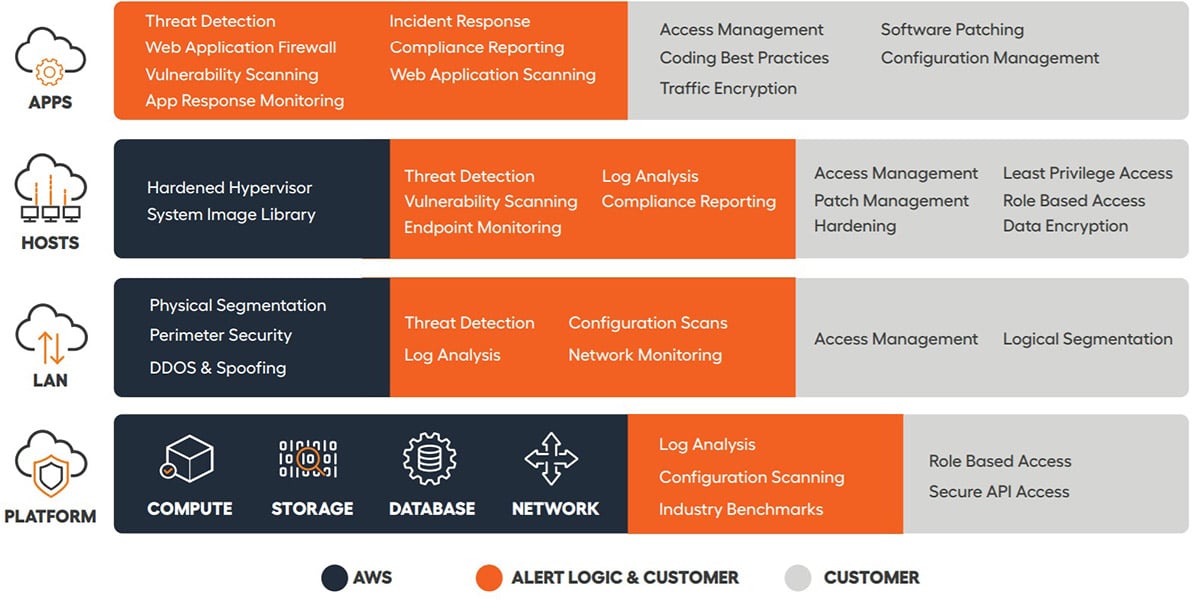
9 AWS Security Best Practices - Alert Logic In order to keep your cloud environment protected against threats, you must update your security policies to your AWS cloud services. This will help you increase visibility and keep your cloud systems protected against the evolving threat landscape. In this post, we're going to look at 9 AWS security best practices to help you with that.
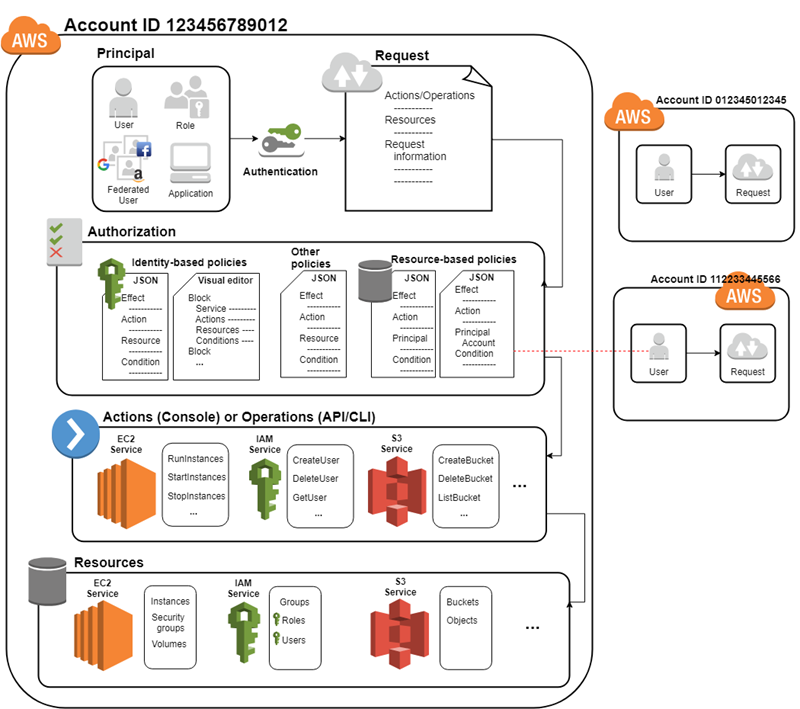
Security best practices in IAM - AWS Identity and Access Management To help secure your AWS resources, follow these best practices for AWS Identity and Access Management (IAM) . Topics Require human users to use federation with an identity provider to access AWS using temporary credentials Require workloads to use temporary credentials with IAM roles to access AWS Require multi-factor authentication (MFA)
AWS Security Best Practices - AWS Security Best Practices AWS Security Best Practices AWS Whitepaper Welcome AWS Security Best Practices PDF RSS Notice: This whitepaper has been archived. For the latest technical information on Security and Compliance, see .
AWS Cloud Security: Best Practices for Financial Services AWS Best practices Cloud Security. Alfredo Pardo. June 29, 2022. According to Sophos, over 70% of organizations hosting their workload on the cloud faced a security incident in 2020. With the increasing number of threats on the horizon, cloud security is becoming more crucial for organizations of all sizes to keep their data secured.
10 AWS Whitepaper Security Best Practices - CLIMB Automated security best practices include setting up identity and access management (IAM) roles, configuring network security groups, and implementing logging and monitoring solutions. Additionally, automated security best practices should be regularly reviewed and updated to keep up with changes in technology and threats. 5.
AWS Security Best Practices - Lepide Blog: A Guide to IT Security ... AWS Security Best Practices. AWS (Amazon Web Services) is the world's most popular public cloud infrastructure provider. They provide on-demand cloud computing platforms to individuals, companies, and governments. Amazon takes security very seriously, and generally does a good job of it, as security is an integral part of its business model.
Learn best practices for securing your AWS account and resources Here are some best practices to consider when securing your account and its resources: Safeguard your passwords and access keys Activate multi-factor authentication (MFA) on the AWS account root user and any users with interactive access to AWS Identity and Access Management (IAM) Limit AWS account root user access to your resources
Security, Identity & Compliance | AWS Architecture Center Best Practices for Security, Identity, & Compliance Learn how to meet your security and compliance goals using AWS infrastructure and services. To learn current AWS recommendations and strategies to use when designing cloud architectures with security in mind, see the Security Pillar - AWS Well-Architected Framework.
26 AWS Security Best Practices to Adopt in Production - Sysdig There are few AWS security best practices to adopt when it comes to S3. 9.-. Enable S3 Block Public Access setting 🟨🟨. Amazon S3 public access block is designed to provide controls across an entire AWS account or at the individual S3 bucket level to ensure that objects never have public access.
AWS Lambda Security Threats and Mitigations - haiderm.com Follow AWS's security best practices, including the AWS Lambda Security Best Practices guide, to help ensure the security of your serverless applications. Secure Lambda function example template. Securing both your AWS Lambda functions and their deployment is important because they are both critical components of your serverless application ...
PDF AWS Security Best Practices - AWS Whitepaper Title: AWS Security Best Practices - AWS Whitepaper Author: Amazon Web Services Created Date: 20221208210247Z
GitHub - bwcx-aws/bp-of-security-on-aws: Best Practices of Security on AWS. Best Practices of Security on AWS. Contribute to bwcx-aws/bp-of-security-on-aws development by creating an account on GitHub.
10 AWS Security Audit Best Practices - CLIMB In this article, we'll discuss 10 AWS security audit best practices that you should consider when conducting an audit. We'll cover topics such as identity and access management, logging and monitoring, and encryption. By following these best practices, you can ensure that your cloud environment is secure and compliant. 1.
🔥 Security Best Practices for AWS Users - azumo.com It is essential that AWS users understand the importance of security in the cloud environment and take the necessary steps to protect their data and resources. This article will provide an overview of security best practices for AWS users, covering topics such as access control, logging and monitoring, encryption, and data protection measures.
Best practices for securing sensitive data in AWS data stores AWS Identity and Access Management (IAM): Define, enforce, and audit user permissions across AWS services, actions, and resources. Detective control: Improve your security posture, reduce the risk profile of your environment, and gain the visibility you need to spot issues before they impact your business.
























.jpg?ixlib=gatsbyFP&auto=compress%2Cformat&fit=max&q=50)



0 Response to "39 aws security best practices"
Post a Comment