45 aws best practices
AWS Lambda Performance Tuning & Best Practices (2022) Performance Results. In an experiment conducted by Alex Casalboni, it was observed that for Two CPU-intensive functions, using the AWS Lambda Power Tuning mechanism results in faster and cheaper experience. Execution time goes from 35s with 128MB to less than 3s with 1.5GB, while being 14% cheaper to run. AWS CDK - Best Practices From The Trenches The logical ID is derived from the id you specify when you instantiate the construct.." — official AWS CDK Best practices. It's always best to be safe than sorry. Mistakes can happen. It takes one naive refactor to a stateful CDK resource (move around constructs, rename logical id, etc.) to delete an entire production database and ...
Establishing your best practice AWS environment The rest of this guide will walk you through the elements of building a secure and productive multi-account AWS environment, often referred to as a “landing zone,” as recommended by AWS. This represents the best practices that can be used to build an initial framework while still allowing for flexibility as your AWS workloads increase over ...

Aws best practices
aws/aws-eks-best-practices - GitHub A best practices guide for day 2 operations, including operational excellence, security, reliability, performance efficiency, and cost optimization. Return to Live Docs. License Summary The documentation is made available under the Creative Commons Attribution-ShareAlike 4.0 International License. See the LICENSE file. Best Practices for Organizational Units with AWS Organizations Jul 21, 2020 · Best practices for setting up your multi-account AWS environment Before getting started, let’s get familiar with a few terms. An organizational unit (OU) is a logical grouping of accounts in your organization, created using AWS Organizations. 13 AWS Security Best Practices - Check Point Software By following this AWS security best practices checklist, it is possible to improve the security of an AWS deployment. Identify Security Requirements 1. Define and Categorize Assets in AWS: It is impossible to secure systems that you don't know exist.
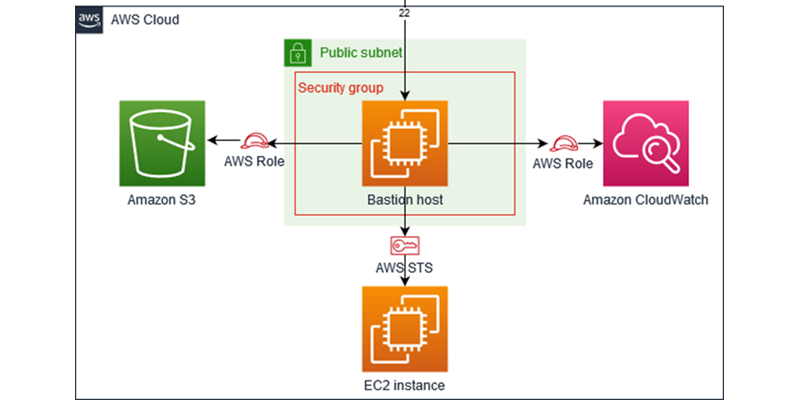
Aws best practices. AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 2 Know the AWS Shared Responsibility Model Amazon Web Services provides a secure global infrastructure and services in the cloud. You can build your systems using AWS as the foundation, and architect an ISMS that takes advantage of AWS features. Multi-account management - AWS Organizations Customers - Amazon Web ... FactSet. FactSet creates flexible, open data and software solutions for over 170,000 of investment professionals around the world, providing instant anytime, anywhere access to financial data and analytics that investors use to make crucial decisions. "Using AWS Organizations, we're able to accelerate development by giving teams their own ... AWS Best Practices: five key approaches - Cloud Academy AWS Best Practices: secure your Applications Sometimes it is better to explain a concept with a picture or diagram rather than with words. The diagram below could be a small scale deployment on AWS. You have a Web Server, an App Server, and a DB server. You should allow access from the outside world only where necessary. PDF Architecting for the loud Amazon Web Services - Architecting for the Cloud: AWS Best Practices Page 5 Design Principles The AWS Cloud includes many design patterns and architectural options that you can apply to a wide variety of use cases. Some key design principles of the AWS Cloud include scalability, disposable resources, automation, loose coupling managed services
Best Practices for Running Apache Kafka on AWS 2.3.2018 · The best practices described in this post are based on our experience in running and operating large-scale Kafka clusters on AWS for more than two years. Our intent for this post is to help AWS customers who are currently running Kafka on AWS, and also customers who are considering migrating on-premises Kafka deployments to AWS. Deploying Databricks on AWS: Key Best Practices to Follow One of the AWS best practices is the focus on security and availability. When deploying Databricks, this focus should be integrated right from the beginning. For effective security and availability, aligning it with the AWS user management to allow one-time IAM will provide access to the environment with appropriate controls. Best practice rules for Amazon Web Services | Trend Micro Ensure AWS Launch Configurations are utilizing active Amazon Machine Images. Launch Configuration Referencing Missing Security Groups Ensure AWS Launch Configurations are utilizing active Security Groups. Multi-AZ Auto Scaling Groups Ensure AWS Auto Scaling Groups utilize multiple Availability Zones to improve environment reliability. Best practices for AWS accounts - AWS Account Management Best practices for AWS accounts. PDF. This section describes best practices that we recommend that you follow with your AWS accounts. They are arranged in the following categories: Topics. Best practices to protect your account's root user; Best ...
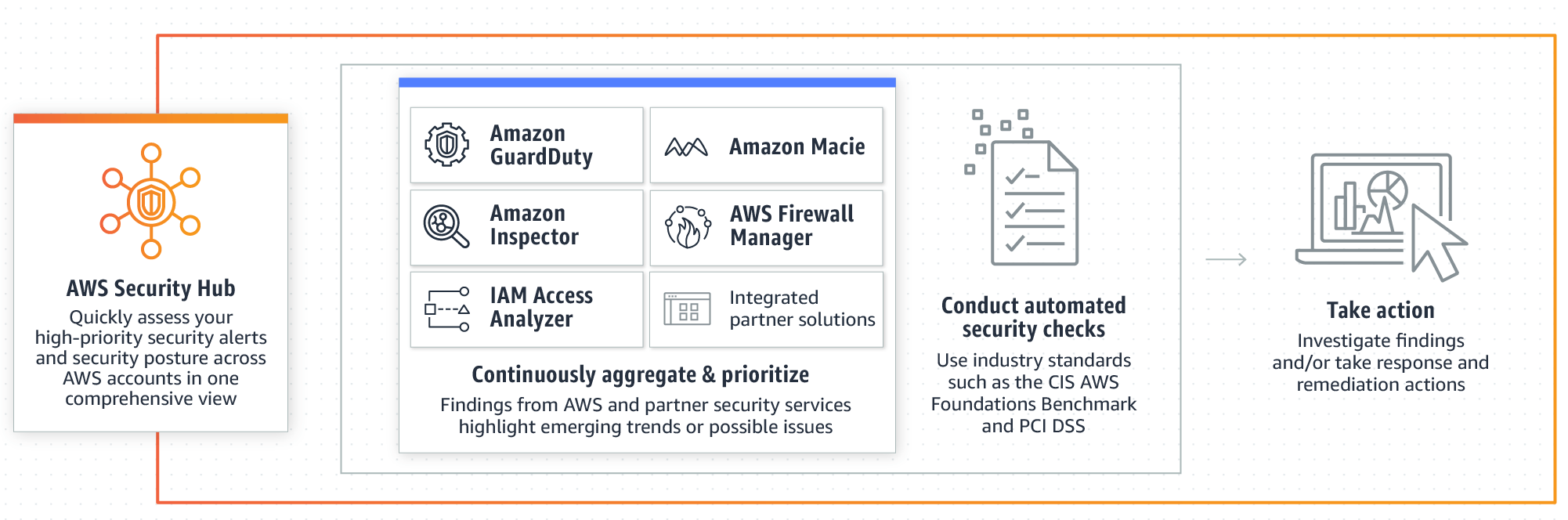
Best Practices for an Iterative Cloud Cost Optimization and Cost ... Best Practices for an Iterative Cloud Cost Optimization and Cost Management Practice. In Amazon's Q3 earnings call, Amazon CFO Brian Olsavsky stated that AWS has seen an uptick in customers focused on controlling costs, and that the company is proactively working to help customers optimize. Given economic uncertainty, cloud customers are ... AWS Monitoring Tools and Best Practices: Monitor What Matters - NetApp AWS Monitoring Best Practices Use Automation Where Possible Create Policies to Define Priority Levels Resolve Problems Early On Use the Cloud to Your Advantage AWS First-Party Monitoring Tools AWS Security Best Practices - AWS Security Best Practices AWS Security Best Practices AWS Whitepaper. Welcome; AWS Documentation AWS Whitepapers AWS Whitepaper. AWS Security Best Practices. PDF. Notice: This whitepaper has been archived. For the latest technical information on ... amazon web services - What are the best practices about cognito and ... AWS limits the number of resource server to 25 (with a maximum of 300) within a single user pool. So in my case, i can only create 25 api until i get blocked. Oauth2 definition of resource server is " The resource server is the OAuth 2.0 term for your API server " and the auth0 is " the server hosting the protected resources.
r/aws - Strategies and best practices to retain sensitive customer data ... Strategies and best practices to retain sensitive customer data in the cloud. Hey everyone! Part of our product requires sensitive customer data to be retained in a DynamoDB database. I'm wondering if some of you can share best practices for this. Currently I have the following in place: - The data is received via html over https from an ...
10 best practices to secure your AWS environment - Medium You need to secure your AWS resources, especially your accounts, from possible attacks. In this article, I want to describe 10 best practices to follow to help you put your mind at peace when ...
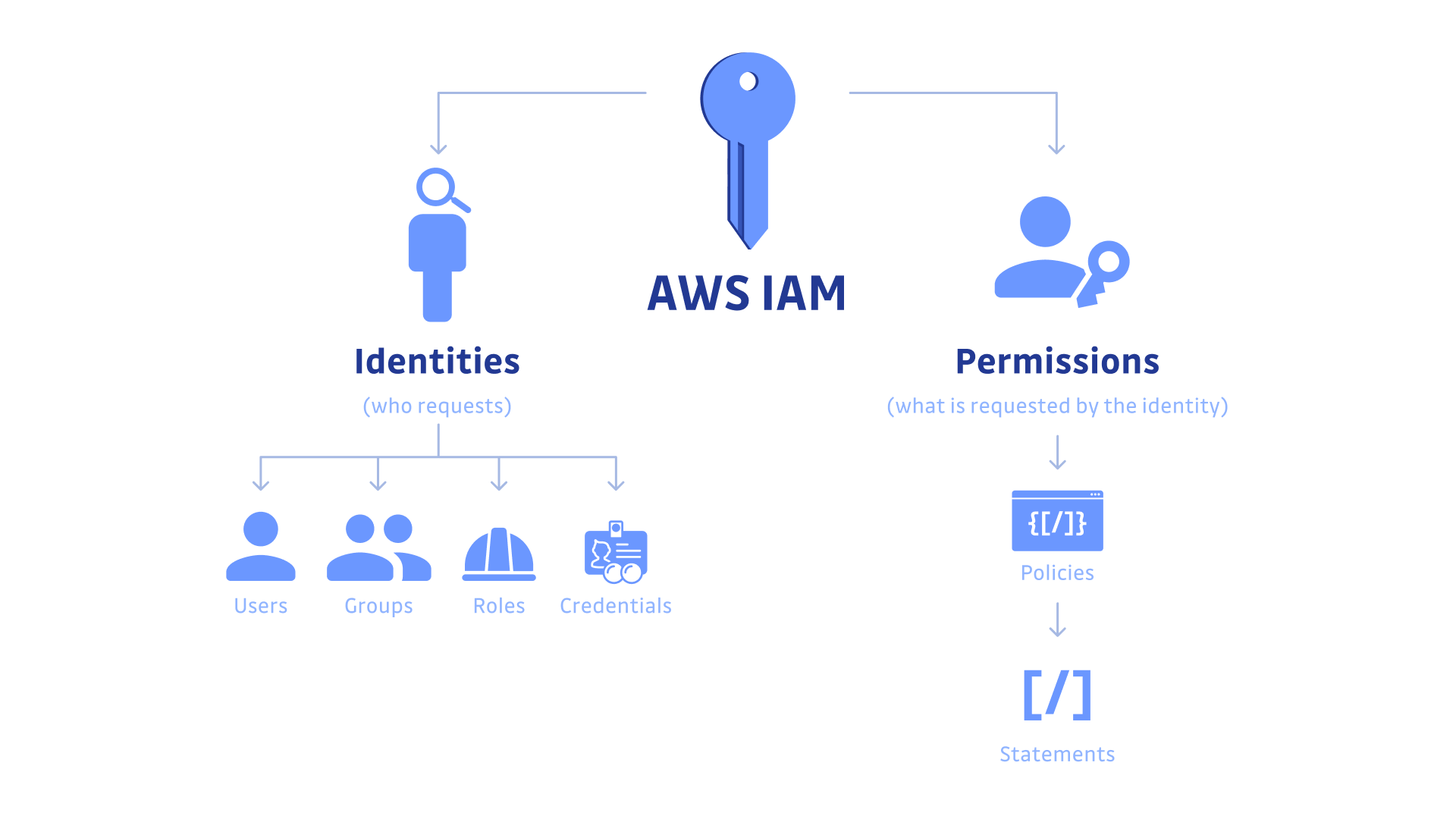
Best practices to protect your account's root user The following are recommended best practices related to the root user of an AWS account. Limit the tasks you perform with the root user You should protect your root user credentials like you would your credit card numbers or any other sensitive secret and use them for only the tasks that require them.
Learn best practices for securing your AWS account and resources Aug 22, 2022 · For more information, see Security best practices in AWS CloudTrail. Use CloudTrail and CloudWatch in conjunction to monitor access key usage and receive alerts for unusual API calls. Activate resource-level logging (for example, at the instance or OS level) and Amazon S3 default bucket encryption .
Security best practices: Scraping with Lambda + S3 : r/aws Security best practices: Scraping with Lambda + S3. hey y'all, I'm relatively new to AWS and attempting to implement a small-scale web scraper using Lambda functions & saving data (HTML files) to an S3 bucket for further analysis. What precautions should I take to ensure I'm not inadvertently introducing malware/malicious files into my ...
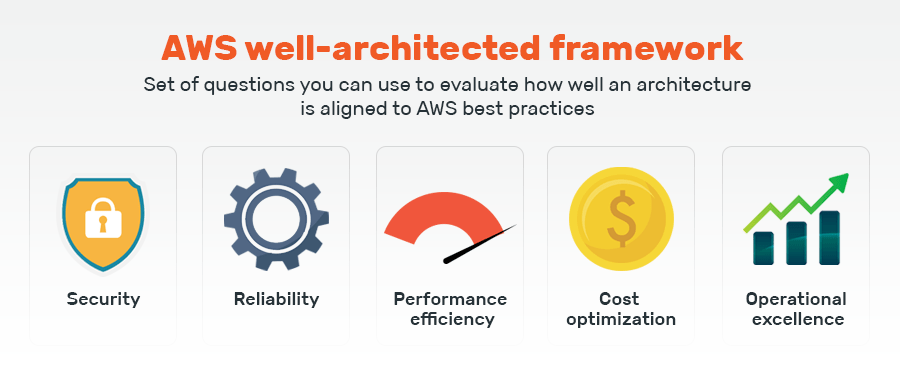
AWS Well-Architected Best Practices | Classroom Training | AWS The AWS Well-Architected Best Practices course will help you learn a consistent approach to evaluate architectures and implement designs from a live instructor. You'll learn how to use the Well-Architected Review process and the AWS Well-Architected Tool to conduct reviews to identify high risk issues (HRIs).
Best practices for deploying Gateway Load Balancer 8.7.2021 · Introduction At re:Invent 2020, we launched Gateway Load Balancer (GWLB), a service that makes it easy and cost-effective to deploy, scale, and manage the availability of third-party virtual appliances. These appliances include firewalls (FW), intrusion detection and prevention systems, and deep packet inspection systems in the cloud. Since the launch, a lot of …
aws glue job: best practice for new data as it comes in? Im new to AWS and glue. I have a glue job that uses a python script to convert a data source into a json formatted file. The new data is sent to us on a monthly basis and so my thought was to trigger the glue job to run every time the data was added to our s3 bucket.
Eight best books to prepare for AWS Certification - Codemithra With an emphasis on hands-on experience, AWS certification evaluates its candidate's skills. The certification provides candidates with best practices. With the help of best practices, the certification is known for its thoroughness. An AWS certification can provide the foundational knowledge and skills you'll need to boost your career.
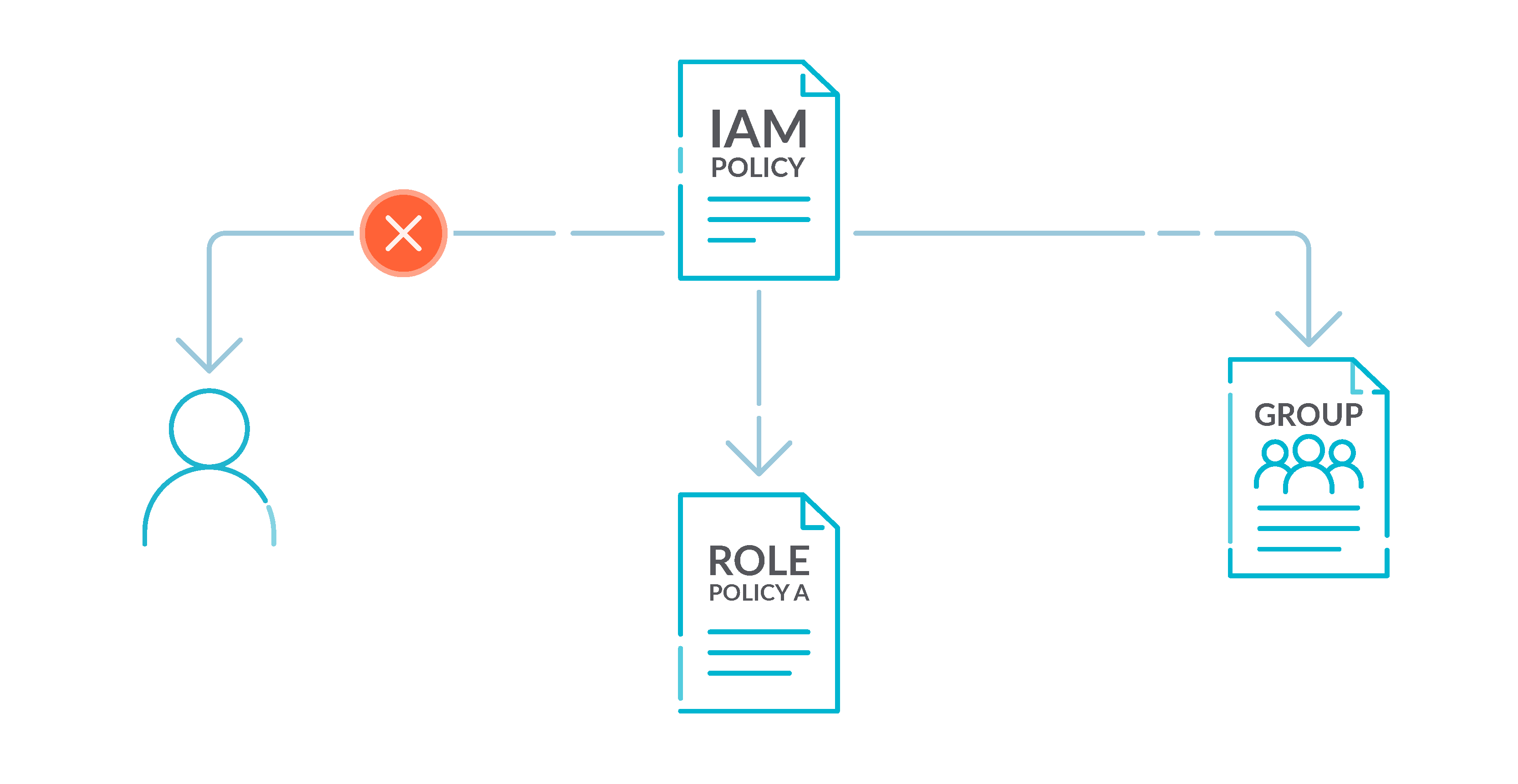
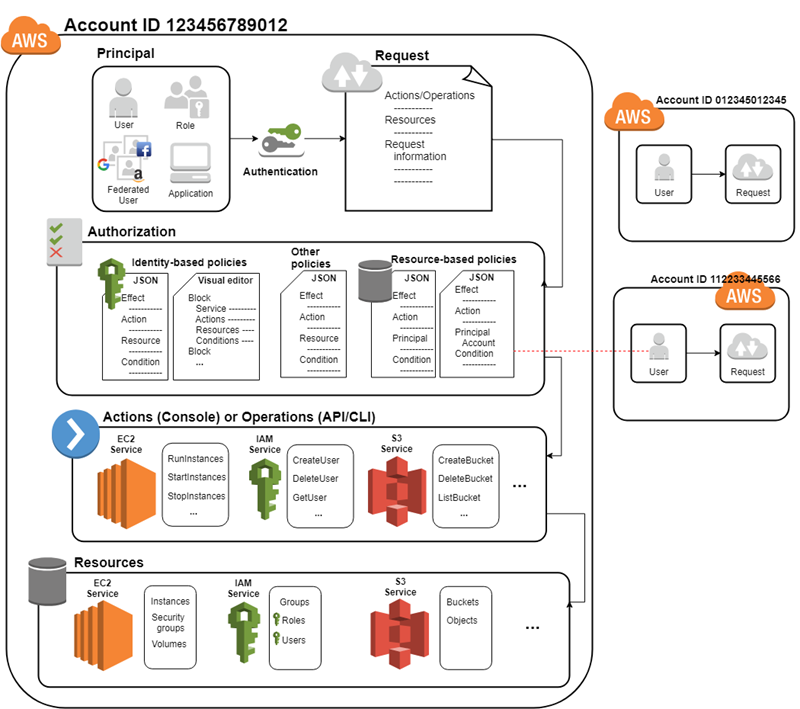
Security best practices in IAM - AWS Identity and Access … Jul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide.
AWS re:Invent 2018: Best Practices for Managing, Retrieving ... - YouTube In this session, learn how to use AWS Secrets Manager to simplify secrets management and empower your developers to move quickly while raising the security b...
Best practices for working with AWS Lambda functions REPORT RequestId: 3604209a-e9a3-11e6-939a-754dd98c7be3 Duration: 12.34 ms Billed Duration: 100 ms Memory Size: 128 MB Max Memory Used: 18 MB. By analyzing the Max Memory Used: field, you can determine if your function needs more memory or if you over-provisioned your function's memory size.. To find the right memory configuration for your …
AWS OpenSearch Best Practices: How to Avoid Common Mistakes Another important best practice, that only 8.2% of users implemented, is restricting the use of wildcards for destructive (delete) operations. Using wildcards could cause accidental deletion of all of your data - and yet 91.8% of people did not avoid that risk by easily disabling deletion of indices via wildcards. Scripts
Best practices for AWS Organizations - AWS Organizations Best practices for AWS Organizations PDF RSS We recommend that you follow these best practices when you create and operate your organization. Topics Best practices for the management account Best practices for member accounts Did this page help you? No Provide feedback Edit this page on GitHub
AWS SYSTEM ADMINISTRATION: BEST PRACTICES FOR SYSADMINS IN By Mike Ryan ... AWS System Administration: Best Practices for Sysadmins in the ISBN: 9781449342579 EAN: 9781449342579 Publication Year: 2018 Type: Textbook Format: Trade Paperback Language: English Publication Name: American Weigh System Administration : Best Practices for Sysadmins in the Amazon Cloud Item Height: 0.8in. Author: Federico Lucifredi, Mike Ryan
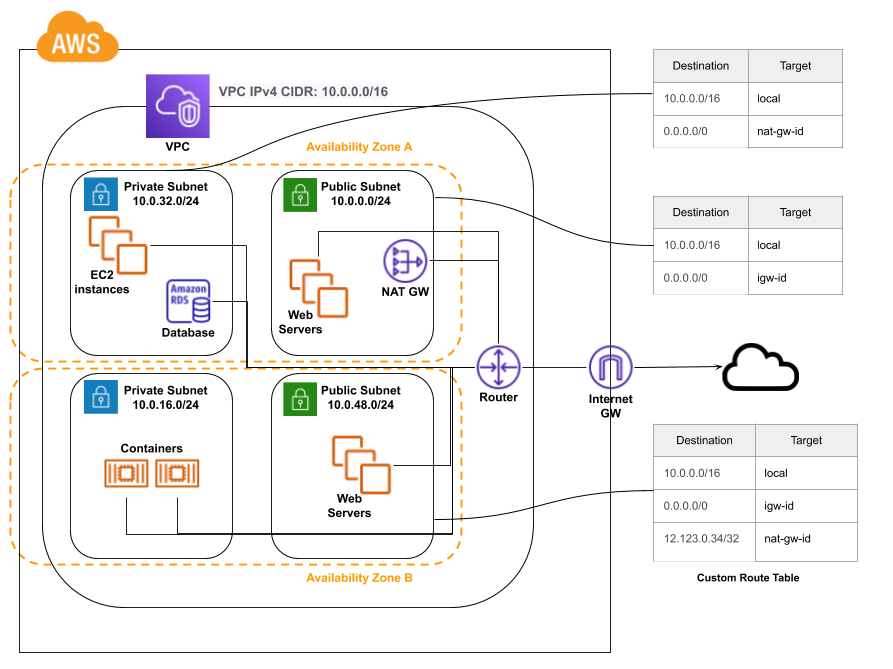
AWS Regions, Availability Zones, and Strategy & Best Practices Best practices to choose an AWS Region . Let's look at some key parameters organizations should consider while choosing an AWS region to get the best results. Proximity and latency: In many cases, it is good practice to opt for the closest possible AWS region. Being in the proximity of the server enhances user experience, cuts down transfer ...
13 AWS Security Best Practices - Check Point Software By following this AWS security best practices checklist, it is possible to improve the security of an AWS deployment. Identify Security Requirements 1. Define and Categorize Assets in AWS: It is impossible to secure systems that you don't know exist.
Best Practices for Organizational Units with AWS Organizations Jul 21, 2020 · Best practices for setting up your multi-account AWS environment Before getting started, let’s get familiar with a few terms. An organizational unit (OU) is a logical grouping of accounts in your organization, created using AWS Organizations.
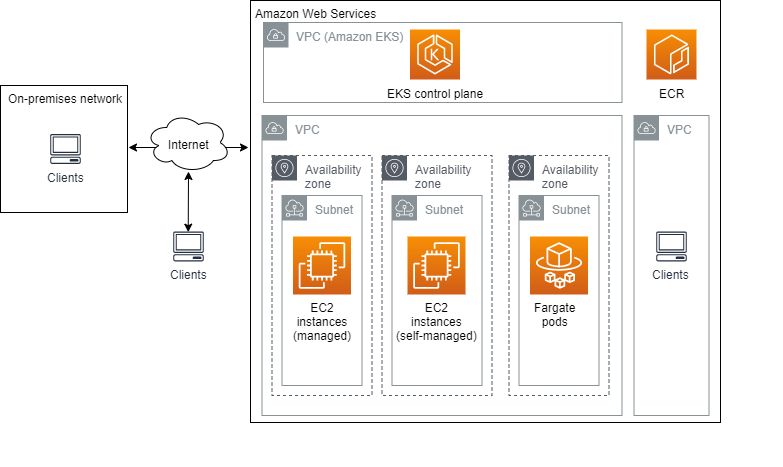
aws/aws-eks-best-practices - GitHub A best practices guide for day 2 operations, including operational excellence, security, reliability, performance efficiency, and cost optimization. Return to Live Docs. License Summary The documentation is made available under the Creative Commons Attribution-ShareAlike 4.0 International License. See the LICENSE file.

![AWS IAM: Best practices [Part 1] – DEVOPS DONE RIGHT](https://blog2opstree.files.wordpress.com/2021/03/image-36.png)





























0 Response to "45 aws best practices"
Post a Comment